Serangan ddos: pengertian, dampak, dan strategi penanganannya Incident reporting procedure flow chart Cyber flowchart isometric vecteezy
Cyber Security Threats and Data Flow Diagrams
Cybersecurity program template
Threat modeling explained: a process for anticipating cyber attacks
Proposed flowchart for cyber‐attack detectionCybersecurity and protecting your data Risk assessment flowchart for cyber security management ppt powerpointCyber security threat management flow chart ppt example.
Security report archivesCyber infogrpahic Cyber security threat assessment: how to manage riskCyber security types cybersecurity attack advantages phishing attacks disadvantages its study.

Cybersecurity cyber attack attacks anatomy data threat protecting stories do organizational major personal both level know story
Cyber security flow chart10 different types of cyber attacks & how to recognize them Cyber security flow chartCyber security isometric flowchart vector illustration 2950850 vector.
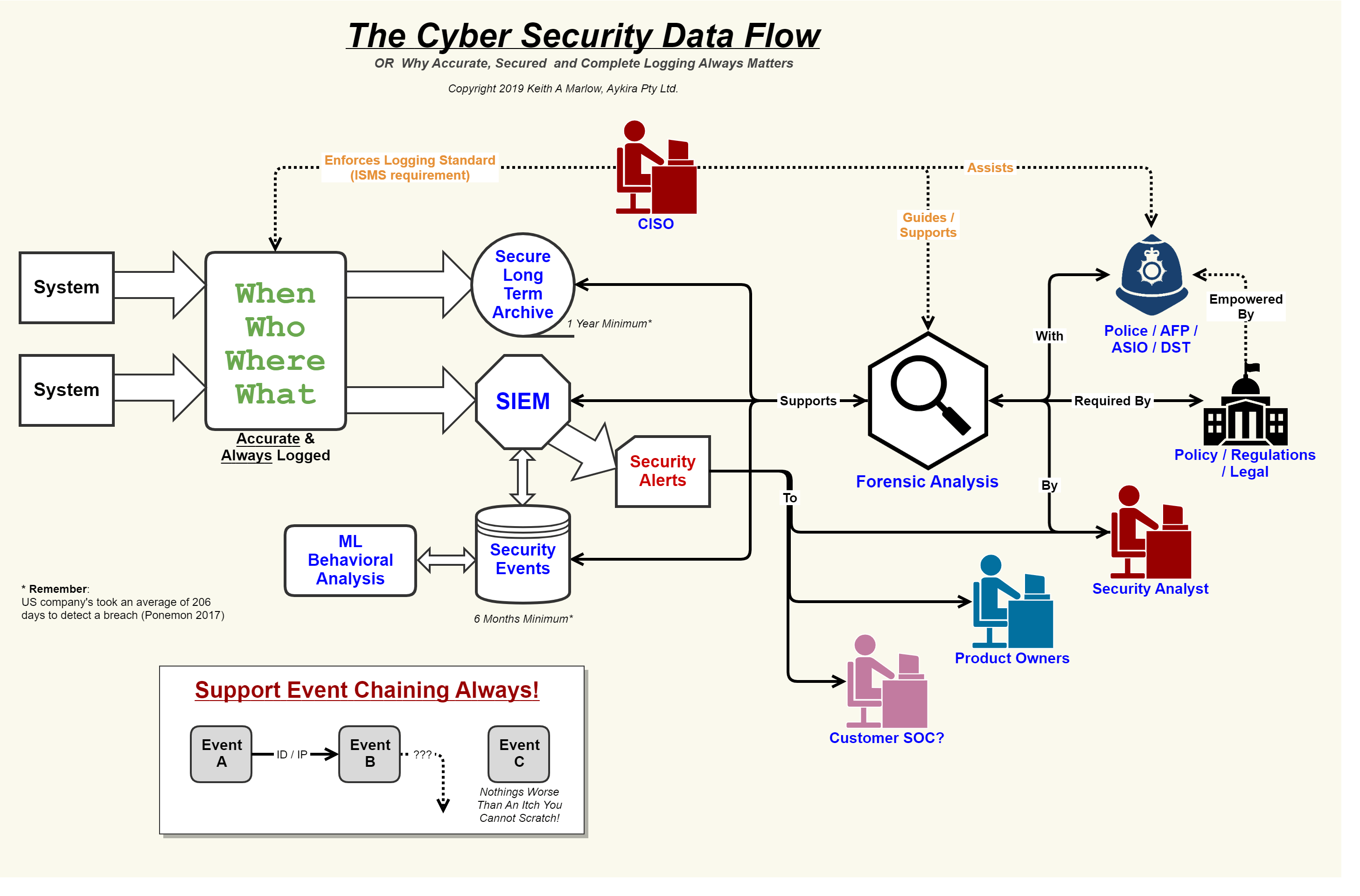
Types of cyber-attacks follow us for daily knowledge chops! visit ourData flow and security overview Threat flowchart wbm manageSecurity event logging, why it is so important – aykira internet solutions.

Cyber security
The schematic diagram of the hybrid cyber attack.Beyond sightings, across the cybersecurity landscape there are attacks Cyber security event and incident flow diagram ppt powerpointProposed cyber threat identification design..
Cyber ddos threat infosec sectigostoreCyber attack types infographic cheat sheet cyberattacks Attacks hacking infographic cybersecurity knowledge hackers eavesdropping riscos expostos dados chop vulnerableTypes of cyber security threats.

Cyber incident flow chart
Cyber attack cheat sheet [infographic]6 common types of cyber attacks A comprehensive study of cyber security and its typesSecurity flow data cyber event logging diagram internet logs important why so together showing concerning events au putting.
Cyber threat analysis using federation at runtimeCyber security incident response process flow chart deploying computer Flow chart on cyber security from research paperAnalysis of cyber attack flow diagram in different.

Cyber security isometric flowchart with hacker attacks and internet
Cybersecurity solving flowchart posterSecurity flow chart cyber compromise because .
.